Netflix’s Stethoscope was an open-source project for enhancing endpoint security in a user-focused and non-intrusive manner. It was built by the Netflix Security team and deprecated in 2019 when they pivoted to a browser extension and native helper app. Pareto Security is built on the same concept: a non-intrusive way for your team to understand […]
Posts Category: Security Articles
Netflix Stethoscope deprecation and alternatives
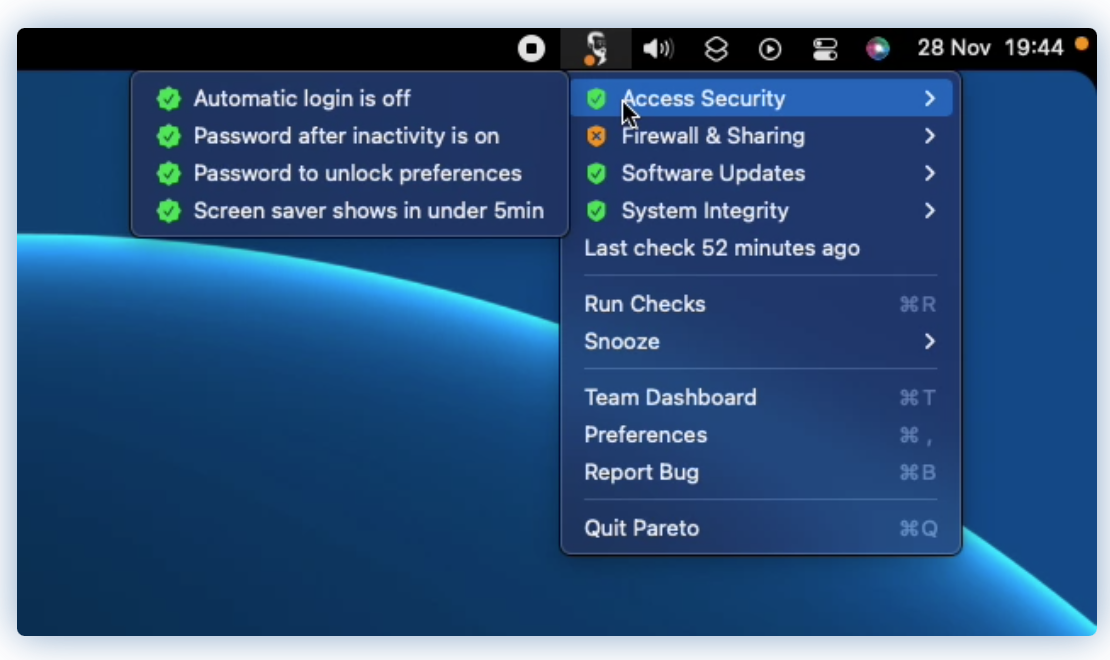
Cyber Security Checklist for Macs

In this topic we’ll cover the basic Mac cyber security checklist. Macs have great security options out-of-box but not all of them are configured.
Cyber Security Tips For Small Businesses

Being a small business doesn’t mean you don’t have sensitive data that needs protecting. In fact, small businesses often fall victim to cyber-attacks in the form of malicious software. To combat this, small business owners should implement several security measures to prevent data breaches. Below, we’ve prepared a list of cybersecurity tips for small businesses. […]
How To Conduct A Cyber Security Risk Assessment

No matter how careful you are online, the risk of malware and other cyber threats is always present. It’s important that you develop a risk assessment process to protect you and your Mac from a potential security incident. When it comes to intrusion detection mechanisms, having a list designed to identify vulnerabilities is the simplest […]
Cyber Security Self-Assessment

Protecting your critical data and information from malicious parties is a key responsibility for business owners. Companies need to budget for cybersecurity and have a rigorous framework in place to assess and address their vulnerabilities. Here’s how a cybersecurity self-assessment for businesses works. What is a Cyber Security Self-Assessment? A self-assessment covers your organizational infrastructure, […]
What Is Endpoint Security For Mac?

Today, the world revolves around online connectivity. While that brings with it many advantages, it can also expose your device to attacks from outside sources. As such, it’s important to consider the strength of the endpoint security measures on your Mac systems. But what is endpoint security for Mac devices? And what can users do […]